
Quantum Computing Cryptocurrency: The Apocalypse Threatens Your Bitcoin Portfolio’s Survival
Quantum Computing Cryptocurrency Attacks Expose Massive Bitcoin Vulnerability
“Q-Day” approaches as quantum computers develop exponentially, with NIST projecting cryptographically relevant quantum computers (CRQCs) emerging between 2030-2035. BlackRock’s unprecedented acknowledgment of quantum threats in their Bitcoin ETF filing signals institutional recognition of this looming catastrophe.
The Quantum Cryptographic Foundation Collapse
Quantum computing cryptocurrency vulnerabilities stem from Shor’s Algorithm, which can efficiently solve the elliptic curve discrete logarithm problem underlying Bitcoin’s ECDSA signatures. Unlike classical computers requiring astronomical timeframes to crack private keys, quantum computers can derive private keys from exposed public keys in polynomial time.
Elliptic Curve Digital Signature Algorithm (ECDSA) forms Bitcoin’s transaction authentication backbone, relying on mathematical problems that quantum computers solve exponentially faster than classical systems. When Bitcoin addresses make outgoing transactions, they expose public keys on the blockchain, creating permanent vulnerabilities that quantum adversaries can exploit retroactively.
SHA-256 mining algorithm faces additional quantum pressure from Grover’s Algorithm, which effectively halves cryptographic security from 256 bits to 128 bits. While less catastrophic than Shor’s Algorithm, Grover’s quantum speedup threatens mining centralization and consensus mechanism integrity.
Critical Attack Vectors and Vulnerability Assessment
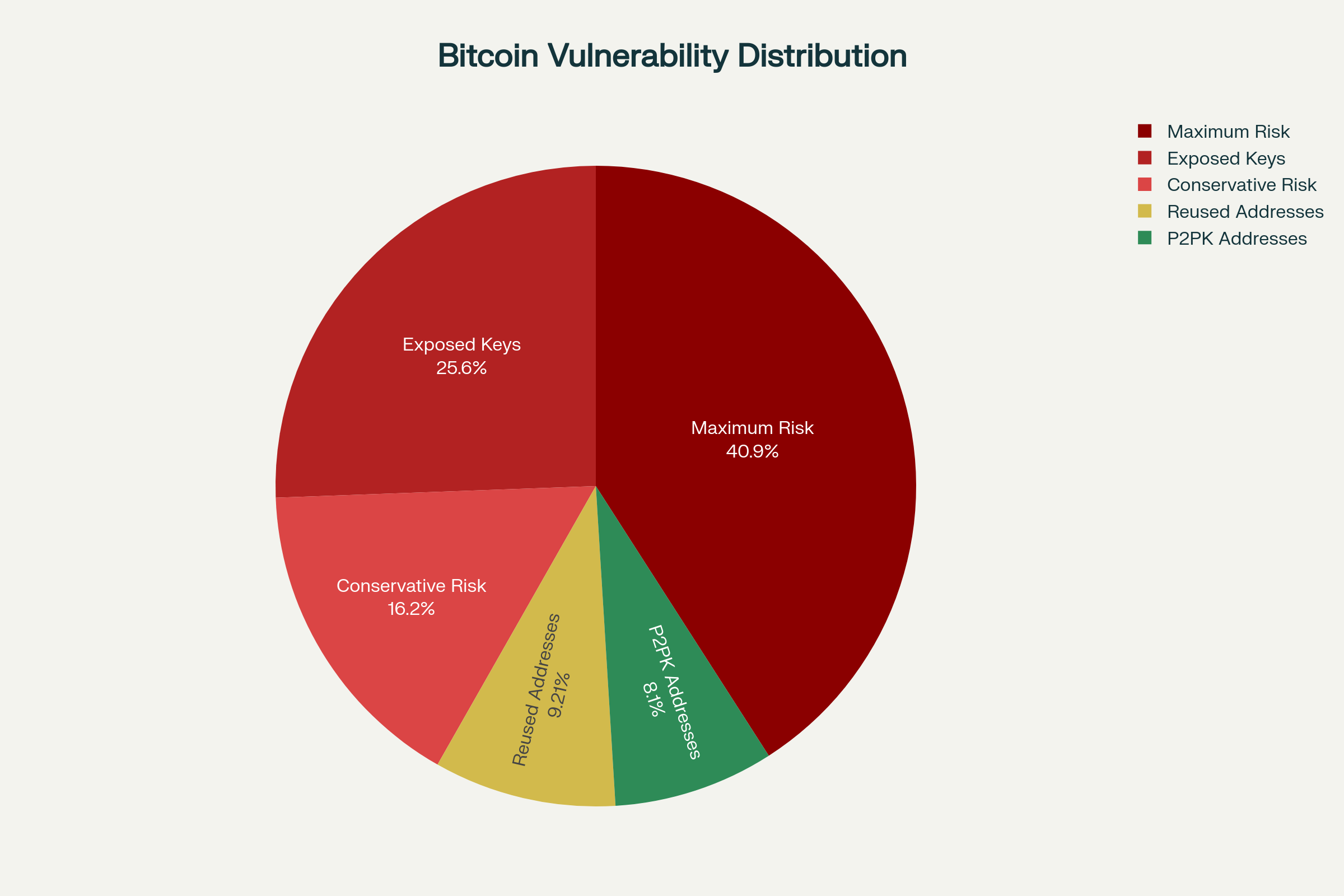
- Pay-to-Public-Key (P2PK) addresses represent the highest vulnerability category, containing approximately 2 million Bitcoin from early network operations. These addresses directly expose public keys on the blockchain, making them immediate targets for quantum decryption attacks.
- Reused address vulnerabilities affect an additional 2.26 million Bitcoin, where multiple transactions have repeatedly exposed the same public keys. Address reuse, while discouraged, remains prevalent among users unaware of quantum implications, creating expanding attack surfaces.
- Taproot (P2TR) script vulnerabilities emerge when complex spending conditions reveal public keys within transaction scripts. Even Bitcoin’s most recent address format contains quantum-vulnerable elements under specific spending scenarios.
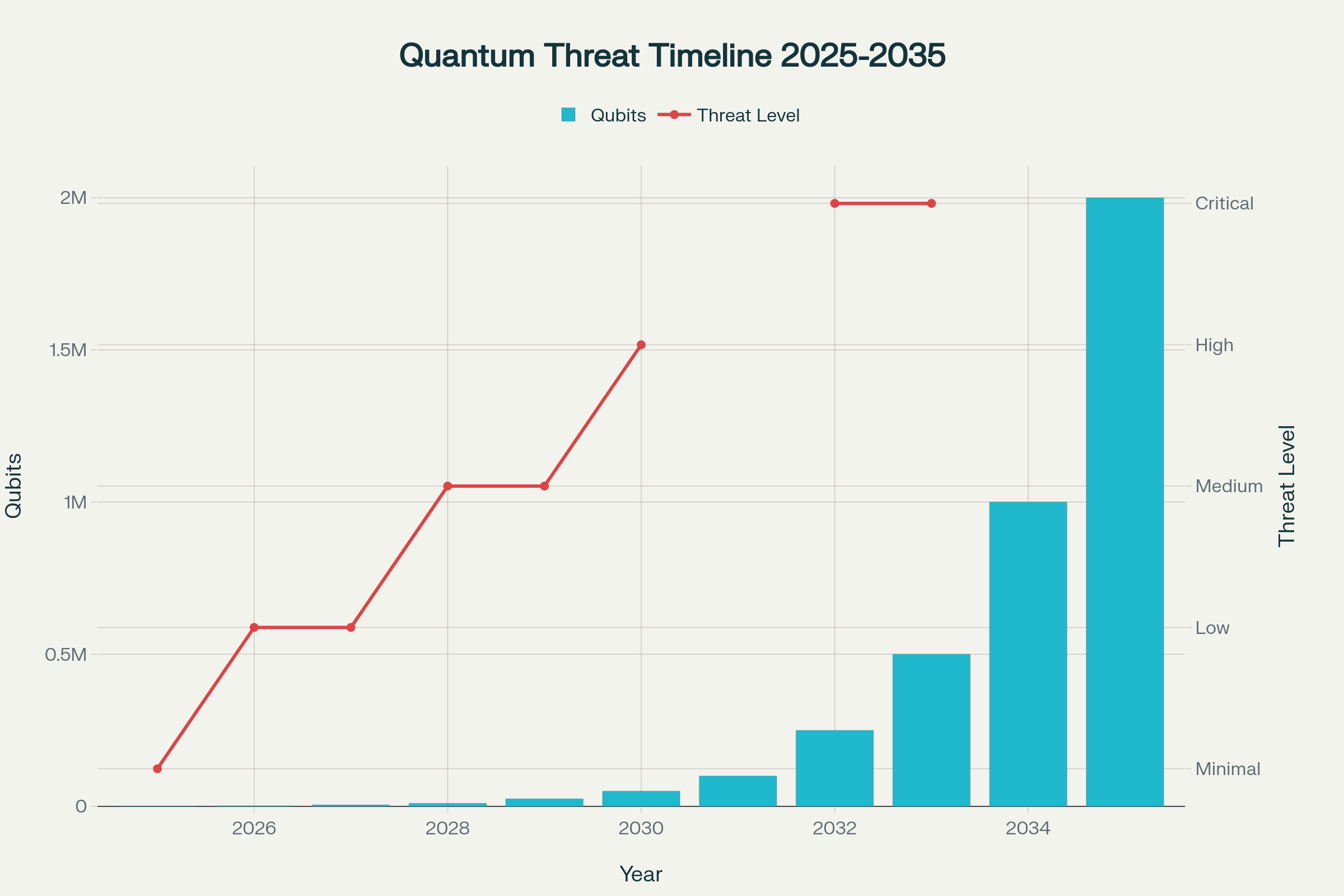
The Quantum Timeline: Exponential Threat Escalation
Current quantum capabilities in 2025 encompass approximately 1,200 qubits in leading systems from IBM, Google, and other quantum pioneers. While insufficient for cryptographic attacks, these systems demonstrate rapid progress toward cryptographically relevant thresholds.
Cryptographically Relevant Quantum Computers (CRQCs) require millions of error-corrected qubits to break Bitcoin’s cryptography practically. IBM’s roadmap targets 100,000-qubit systems by 2030, with fault-tolerant quantum computers expected by 2040.
Q-Day acceleration factors include breakthrough discoveries, increased quantum investment, and potential classified quantum capabilities that could dramatically compress expected timelines. The “harvest now, decrypt later” strategy means adversaries may already be collecting encrypted data for future quantum decryption.
| Quantum Threat Phase | Timeline | Qubit Threshold | Bitcoin Impact | Market Response |
|---|---|---|---|---|
| Experimental Phase | 2025-2027 | 1,200-5,000 | Monitoring required | Academic research |
| Warning Phase | 2028-2029 | 10,000-25,000 | Migration urgency | Protocol development |
| Danger Phase | 2030-2032 | 50,000-250,000 | Active threat | Emergency updates |
| Critical Phase | 2033-2035 | 500,000-2M | Cryptographic break | System transformation |
Post-Quantum Cryptography Defense Strategies
Bitcoin Improvement Proposals (BIPs) under development include BIP-360 implementing Pay-to-Quantum-Resistant-Hash (P2QRH) addresses that use quantum-safe hash functions instead of exposed public keys. This hybrid approach maintains Bitcoin’s existing architecture while adding quantum protection layers.
SPHINCS+ signature integration through proposed OP_SPHINCS opcodes would enable hash-based digital signatures resistant to quantum attacks. Unlike lattice-based alternatives, hash-based cryptography relies on well-understood cryptographic primitives with proven quantum resistance.
Implementation Framework and Migration Strategies
Three-phase transition planning proposed by Bitcoin developers establishes systematic quantum resistance adoption. Phase one restricts new transactions to quantum-resistant addresses, phase two invalidates legacy address spending, and phase three provides recovery mechanisms for stranded funds.
Immediate protection measures include avoiding address reuse, migrating funds from P2PK addresses to newer formats, and monitoring quantum computing developments for acceleration signals. Users should prioritize fresh addresses for each transaction to minimize public key exposure.
Institutional preparation strategies require comprehensive quantum risk assessments, post-quantum cryptography integration timelines, and contingency planning for accelerated quantum breakthroughs. Large Bitcoin holders face particular urgency due to their systemic market impact during quantum transitions.
Audit existing Bitcoin holdings for quantum vulnerability exposure
Migrate funds from P2PK and reused addresses to modern formats
Monitor quantum computing milestones and acceleration indicators
Prepare post-quantum cryptography integration plans and timelines
Develop quantum-safe backup strategies and emergency protocols
The Financial Apocalypse Scenario and Market Implications
The quantum computing cryptocurrency threat extends beyond technical vulnerabilities to encompass systemic financial risks that could destabilize global markets. Conservative estimates suggest 4-10 million Bitcoin face quantum vulnerability, representing $200-400 billion in current market value. This massive exposure creates unprecedented scenarios for market manipulation, wealth redistribution, and confidence collapse.
Quantum supremacy announcement effects could trigger immediate market panic even before practical attacks become feasible. Historical precedent shows cryptocurrency markets responding dramatically to security concerns, with quantum computing breakthroughs potentially causing more severe disruptions than traditional vulnerabilities.
Game theory implications emerge as quantum-capable actors face choices between profitable attacks and market preservation. Sophisticated adversaries might prefer extracting maximum value through strategic market timing rather than immediate cryptocurrency theft, creating complex threat dynamics that traditional security models cannot address.
The “quantum winter” scenario describes potential cryptocurrency ecosystem collapse if quantum resistance implementation fails or arrives too late. Legacy cryptocurrencies without quantum protection could face permanent abandonment, while quantum-safe alternatives emerge as replacements in a fundamentally transformed digital asset landscape.
Institutional responses already demonstrate quantum awareness integration, with major financial institutions updating risk assessments and compliance frameworks. BlackRock’s ETF filing acknowledgment signals broader institutional preparation for quantum-resistant cryptocurrency evaluation and potential portfolio rebalancing.
The quantum apocalypse threatens not just individual Bitcoin portfolios but the entire cryptocurrency ecosystem’s foundational security assumptions. Preparation begins now—before quantum computers achieve cryptographic relevance and transform digital asset security from theoretical concern into existential crisis.
Organizations and individuals holding significant cryptocurrency positions must immediately assess quantum vulnerability, implement migration strategies, and prepare for the post-quantum cryptocurrency era. The quantum apocalypse approaches with mathematical inevitability—survival depends on proactive defense rather than reactive scrambling.
FAQ
Q: When will quantum computers be powerful enough to break Bitcoin’s encryption and threaten cryptocurrency portfolios?
A: Cryptographically relevant quantum computers (CRQCs) are projected to emerge between 2030-2035, with “Q-Day” representing the moment quantum systems can break current encryption. IBM’s roadmap targets 100,000-qubit systems by 2030, while experts estimate millions of error-corrected qubits needed for practical cryptographic attacks.
Q: How much Bitcoin is actually vulnerable to quantum computing attacks?
A: Conservative estimates indicate 4-10 million Bitcoin face quantum vulnerability, representing 19-48% of the total supply. Approximately 2 million Bitcoin in P2PK addresses and 2.26 million in reused addresses show highest vulnerability, with total exposed public keys affecting 6.26 million Bitcoin.
Q: What are the NIST post-quantum cryptography standards and how do they protect cryptocurrency?
A: NIST released three post-quantum standards in August 2024: FIPS 203 (CRYSTALS-Kyber), FIPS 204 (CRYSTALS-Dilithium), and FIPS 205 (SPHINCS+). These lattice-based and hash-based algorithms resist both classical and quantum attacks, providing foundation for quantum-safe cryptocurrency implementations.
Q: Can Bitcoin be upgraded to resist quantum computing attacks before Q-Day arrives?
A: Bitcoin developers are proposing quantum-resistant upgrades including BIP-360 (P2QRH addresses) and OP_SPHINCS integration. The three-phase transition plan would gradually migrate to quantum-safe addresses while maintaining network compatibility, requiring community consensus and implementation before 2030.
Q: Should cryptocurrency investors sell their Bitcoin holdings due to quantum computing threats?
A: Rather than panic selling, investors should assess their quantum vulnerability exposure and implement protection strategies. Priority actions include migrating funds from vulnerable address types, avoiding address reuse, and monitoring quantum computing developments while supporting post-quantum cryptocurrency evolution.







