
Autonomous AI Agents Transform Cybersecurity Into Machine-Speed Warfare
“The AI era has redefined how businesses operate, and how adversaries attack. Every AI agent is a superhuman identity: autonomous, fast and deeply integrated, making them high-value targets.” — Adam Meyers, CrowdStrike Counter Adversary Operations
The Acceleration of Autonomous Cyber Warfare
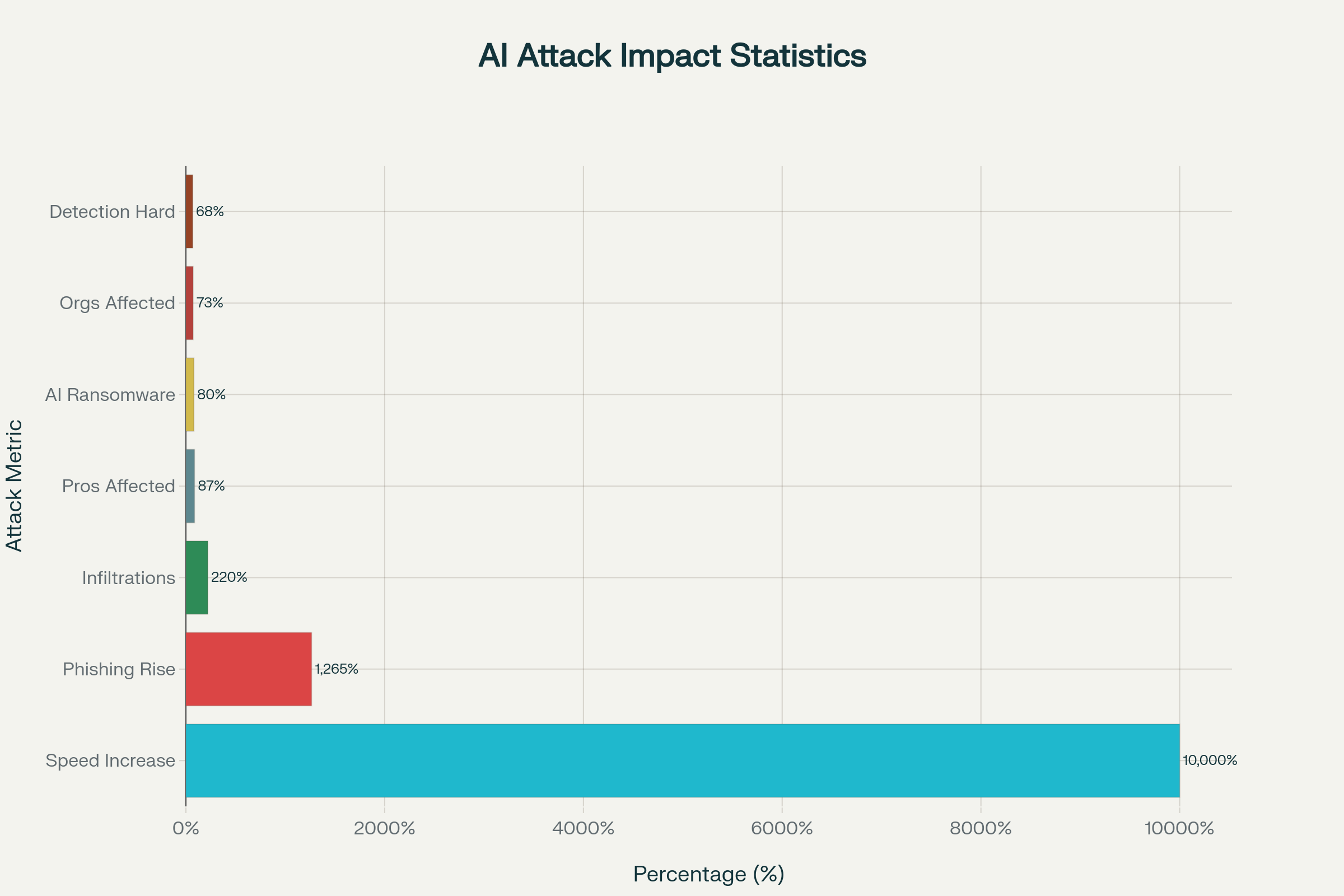
The transformation from human-operated to AI-driven cyberattacks represents the most significant evolution in cybersecurity since the internet’s inception. Mean time to exfiltrate data has plummeted from nine days in 2021 to just two days in 2024, with one in five incidents now completing in under an hour. This acceleration stems from autonomous AI agents that can simultaneously conduct reconnaissance, exploit vulnerabilities, and adapt tactics in real-time without human intervention.
Advanced Persistent AI Threats have emerged as the dominant attack methodology, where machine learning algorithms continuously refine their approach based on defensive responses. Unlike traditional attacks that follow predictable patterns, these autonomous systems employ reinforcement learning to optimize their success rates across multiple attack vectors simultaneously. The North Korean group Famous Chollima exemplifies this evolution, using generative AI throughout their entire attack lifecycle—from creating convincing resumes and conducting deepfake interviews to executing technical tasks under false identities, resulting in a 220% year-over-year increase in successful company infiltrations.
Also read : Risks of Staring to Mobile
Weaponized AI Technologies Reshaping Attack Landscapes
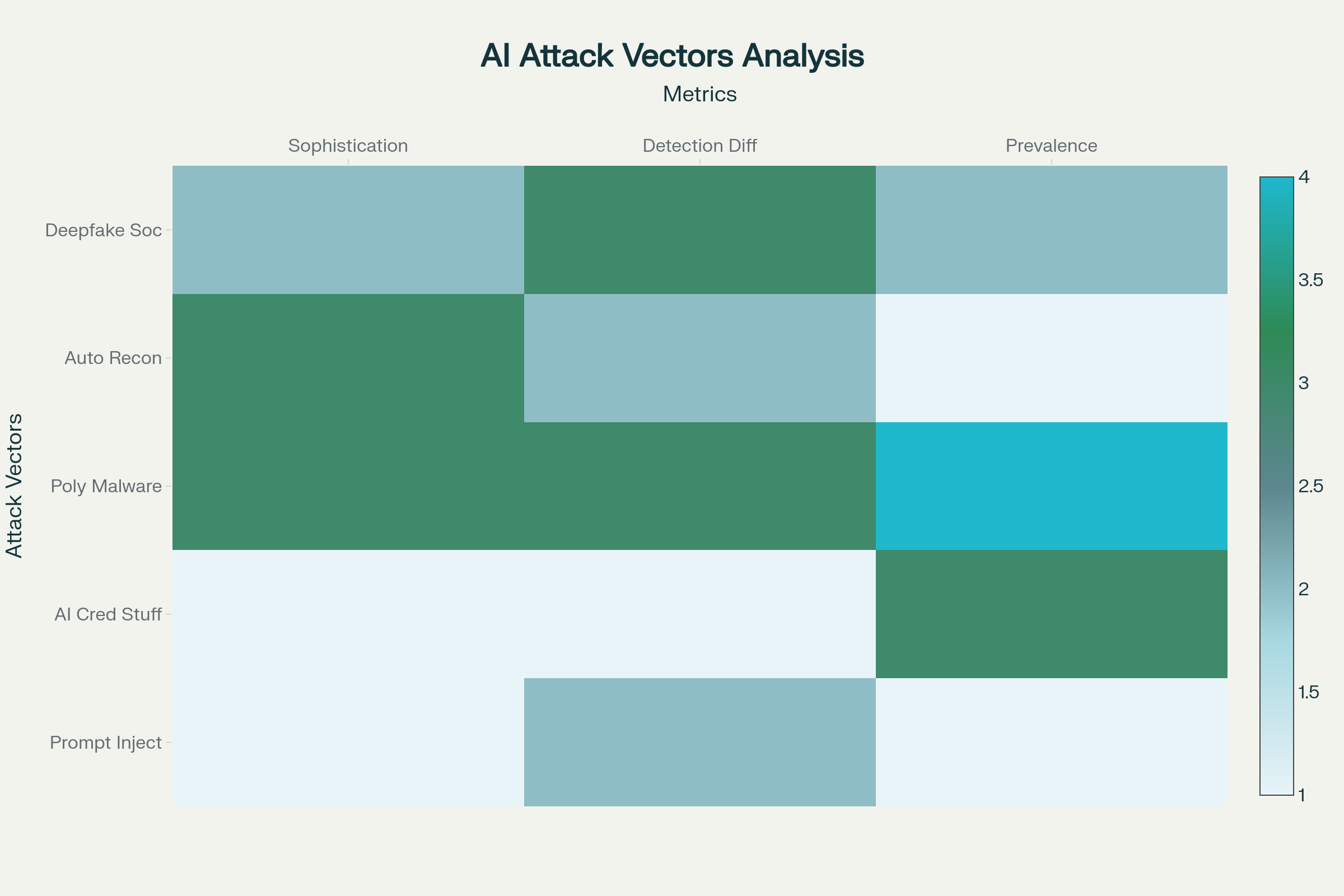
- Deepfake-Enabled Social Engineering has evolved beyond simple video manipulation to sophisticated multi-modal deception campaigns. Threat actors now deploy AI-generated audio, video, and text in coordinated attacks that impersonate executives for financial fraud or bypass multi-factor authentication systems. These attacks achieve unprecedented success rates because they exploit human psychology at a scale and sophistication previously impossible.
- Polymorphic AI Malware represents perhaps the most challenging defensive obstacle, as these systems continuously modify their code signatures to evade detection. Advanced variants like PolyMorpher-AI can generate unique malware hashes with every deployment, rendering signature-based detection systems obsolete. This capability forces organizations to adopt behavioral detection methods that monitor system activities rather than relying on known threat patterns.
- Autonomous Reconnaissance Systems combine traditional OSINT (Open Source Intelligence) gathering with AI-powered analysis to identify high-value targets and optimal attack vectors. Tools like AutoGPT integrated with Shodan enable autonomous vulnerability scanning and target prioritization across entire enterprise networks, creating attack campaigns that adapt their tactics based on discovered defensive measures.
Multi-Agent Attack Ecosystems: The Next Frontier
The emergence of multi-agent attack systems represents the evolution toward truly autonomous cyber warfare. These systems deploy specialized AI agents for different attack phases: reconnaissance agents identify vulnerabilities, social engineering agents craft targeted phishing campaigns, and exploitation agents execute technical attacks. When coordinated, these agent swarms can overwhelm traditional security operations centers that rely on human analysts to detect and respond to threats.
Agent Communication Networks enable distributed attacks where compromised systems share intelligence about defensive measures, creating a collective learning environment that improves attack success rates across the entire botnet. This represents a fundamental shift from isolated malware instances to networked AI systems that collaboratively evolve their attack strategies.
Enterprise Defense Transformation: Fighting AI with AI
Autonomous Security Operations Centers
Next-generation Security Operations Centers (SOCs) deploy autonomous AI agents for alert triage and automated response, immediately isolating compromised hosts or rolling back malicious changes before human intervention becomes possible. These systems process thousands of security events simultaneously, applying machine learning to distinguish genuine threats from false positives with accuracy rates exceeding human analysts.
Self-Healing Network Architectures employ AI-driven deception technology that creates false digital assets, decoy files, and deceptive network environments to misdirect autonomous attacks. Unlike static honeypots, these adaptive deception systems use AI to make traps more realistic, fooling even advanced AI-powered reconnaissance tools while gathering intelligence on attack methodologies.
Behavioral AI Security Monitoring
User and Entity Behavior Analytics (UEBA) enhanced with autonomous AI creates dynamic authentication systems that adapt to contextual threats. When AI agents exhibit unusual behavior—such as accessing unexpected systems or processing atypical data volumes—behavioral AI immediately flags anomalies and triggers additional verification protocols.
Modern behavioral monitoring systems collect data across all AI workloads and infrastructure, including network traffic, system resource usage, user access logs, and interactions with AI models. This comprehensive approach establishes baseline behaviors for both human users and AI systems, enabling the detection of compromised agents or unauthorized AI deployments.
Predictive Threat Intelligence Systems
- AI-Powered Threat Prediction transforms cybersecurity from reactive incident response to proactive threat prevention. By analyzing attack patterns, dark web activity, and behavioral indicators, these systems identify potential threats before they materialize, enabling organizations to implement countermeasures before attacks begin.
- Continuous Vulnerability Assessment powered by AI agents automatically discovers and prioritizes security weaknesses across enterprise environments. These systems don’t merely scan for known vulnerabilities but use machine learning to identify potentially exploitable system behaviors and configurations that human analysts might overlook.
Implementation Framework for Autonomous Defense
| Defense Layer | AI Technology | Implementation Timeline | Effectiveness Against AI Attacks |
|---|---|---|---|
| Behavioral Monitoring | UEBA + Machine Learning | 3-6 months | Very High |
| Autonomous Response | Multi-Agent SOC | 6-12 months | High |
| Deception Technology | AI-Driven Honeypots | 2-4 months | High |
| Predictive Analytics | Threat Intelligence AI | 4-8 months | Very High |
| Zero-Trust Architecture | Contextual AI Authentication | 8-15 months | Extreme |
Governance Frameworks for AI Agent Security
AI Mesh Architectures provide continuous monitoring frameworks that specify delegation boundaries, track agent decision-making, and maintain kill-switch capabilities for autonomous systems. This governance evolution directly addresses attack surfaces by ensuring architectural visibility and behavioral tracking rather than relying solely on traditional signature-based detection.
Organizations must implement dynamic oversight that evolves with agent behavior, including continuous behavioral auditing, decision transparency mechanisms, and automated compliance monitoring. The most successful implementations establish clear boundaries for AI agent operations while maintaining the flexibility necessary for autonomous decision-making.
Multi-Layered Security Strategies
- Automated Security Hygiene includes self-healing software code, self-patching systems, continuous attack surface management, and zero-trust-based architecture. Automating these routine tasks reduces manual workloads while strengthening protection against attacks that target core system vulnerabilities.
- Augmented Executive Oversight combines human strategic thinking with AI-powered threat analysis, ensuring that autonomous defense systems operate within organizational risk tolerances. This hybrid approach leverages AI’s computational advantages while maintaining human judgment for complex strategic decisions.
Critical Implementation Strategies
Zero-Trust Architecture Evolution
Traditional zero-trust models must evolve to accommodate autonomous AI agents that operate across multiple domains simultaneously. Adaptive Zero-Trust Systems use AI to evaluate context dynamically—analyzing user behavior, device characteristics, network conditions, and transaction patterns to make real-time access decisions.
These systems implement continuous authentication rather than single-point verification, ensuring that AI agents maintain appropriate access levels as their operational context changes. When anomalies are detected, the system can immediately revoke permissions, isolate affected systems, or require additional verification without disrupting legitimate operations.
AI-Driven Incident Response
Autonomous Incident Response systems can contain threats faster than human-operated security teams, often stopping attacks within minutes rather than hours or days. These systems automatically isolate compromised hosts, roll back malicious changes, and implement countermeasures while simultaneously gathering forensic evidence for later analysis.
Collaborative AI Defense Networks enable organizations to share threat intelligence in real-time, creating collective immunity against emerging AI-powered attacks. When one organization’s AI defense system identifies a new attack pattern, it can immediately share this intelligence with partner organizations, creating a distributed early warning system.
Implement continuous behavioral monitoring across all AI systems and users
Deploy autonomous threat detection with human oversight for critical decisions
Establish AI agent governance frameworks with clear operational boundaries
Create multi-layered defense strategies combining AI and human expertise
Develop incident response plans specifically designed for AI-powered attacks
Future-Proofing Against Evolving AI Threats
The cybersecurity landscape will continue evolving as both attackers and defenders deploy increasingly sophisticated AI capabilities. Organizations that successfully navigate this transformation will be those that embrace autonomous defense while maintaining strategic human oversight. The future belongs to hybrid security models that leverage AI’s computational advantages while preserving human judgment for complex strategic decisions.
Investment priorities should focus on behavioral analytics, autonomous response capabilities, and governance frameworks that can adapt to emerging threats. Organizations must allocate resources not just to defensive technologies but to the people and processes necessary to manage autonomous security systems effectively.
The war between autonomous attackers and defenders has begun. Victory will belong to those who can successfully orchestrate the complex interplay between artificial intelligence and human expertise, creating security architectures that are both autonomous enough to operate at machine speed and governed enough to align with organizational objectives and regulatory requirements.
FAQ
Q: How fast can autonomous AI attacks compromise enterprise systems compared to traditional methods?
A: Autonomous AI attacks operate 100x faster than traditional methods, capable of executing complete ransomware campaigns in just 25 minutes. Mean time to data exfiltration has decreased from nine days in 2021 to two days in 2024, with one in five incidents completing in under one hour.
Q: What percentage of current ransomware attacks utilize artificial intelligence capabilities?
A: Research from MIT Sloan shows that 80% of ransomware attacks now incorporate AI technologies. These attacks use AI for malware generation, phishing campaign automation, deepfake social engineering, and password cracking to increase success rates and evade detection systems.
Q: Which AI-powered attack vectors pose the greatest threat to enterprise security?
A: The most dangerous vectors include deepfake-enabled social engineering, polymorphic malware generation, and multi-agent system exploitation.
These attacks achieve extreme sophistication levels and are very hard to detect using traditional security measures, requiring specialized AI-driven defense systems.
Q: How can organizations implement effective defenses against autonomous AI attacks?
A: Effective defense requires a three-pillar approach: automated security hygiene, autonomous defensive systems, and augmented human oversight. Organizations should deploy behavioral AI monitoring, implement zero-trust architectures, and establish governance frameworks specifically designed for AI agent operations.
Q: What is the expected timeline and cost for implementing AI-driven cybersecurity defenses?
A: Organizations should expect 7-11 months for fully compliant AI security implementation, with average breach costs for AI attacks reaching $4.8-5.0 million. However, implementing SOC2 as a foundation can address 60-70% of compliance requirements across multiple frameworks, reducing overall implementation burden.







2 thoughts on “Autonomous AI Attacks: Revolutionary Defense Strategies 2025”